COMPTIA NEWS: SY0-401 Exam Questions has been Updated Today! Get Latest SY0-401 VCE and SY0-401 PDF Instantly! Welcome to Download the Newest Braindump2go SY0-401 VCE&SY0-401 PDF Dumps: http://www.braindump2go.com/sy0-401.html (1220 Q&As)
Important News: CompTIA SY0-401 Exam Questions are been updated recently! Braindumo2go offers the latest up-to-date SY0-401 Dumps for free instant download which helps you pass SY0-401 Exam in a short time! Our SY0-401 Exam Dumps has two version: SY0-401 PDF Dumps,SY0-401 VCE Dumps! Choose one of them according to your own need! 100% New SY0-401 Exam Questions from CompTIA Official Exam Center! 100% Pass CompTIA SY0-401 Exam!
Exam Code: SY0-401
Exam Name: CompTIA Security+
Certification Provider: CompTIA
Corresponding Certification: CompTIA Security+
SY0-401 Dump,SY0-401 PDF,SY0-401 VCE,SY0-401 Braindump,SY0-401 Study Guide,SY0-401 Study Guide PDF,SY0-401 Objectives,SY0-401 Practice Test,SY0-401 Practice Exam,SY0-401 Performance Based Questions,SY0-401 Exam Questions,SY0-401 Exam Dumps,SY0-401 Exam PDF,SY0-401 Dumps Free,SY0-401 Dumps PDF

QUESTION 121
A company is preparing to decommission an offline, non-networked root certificate server. Before sending the server’s drives to be destroyed by a contracted company, the Chief Security Officer (CSO) wants to be certain that the data will not be accessed. Which of the following, if implemented, would BEST reassure the CSO? (Select TWO).
A. Disk hashing procedures
B. Full disk encryption
C. Data retention policies
D. Disk wiping procedures
E. Removable media encryption
Answer: BD
Explanation:
B: Full disk encryption is when the entire volume is encrypted; the data is not accessible to someone who might boot another operating system in an attempt to bypass the computer’s security. Full disk encryption is sometimes referred to as hard drive encryption.
D: Disk wiping is the process of overwriting data on the repeatedly, or using a magnet to alter the magnetic structure of the disks. This renders the data unreadable.
QUESTION 122
Identifying residual risk is MOST important to which of the following concepts?
A. Risk deterrence
B. Risk acceptance
C. Risk mitigation
D. Risk avoidance
Answer: B
Explanation:
Risk acceptance is often the choice you must make when the cost of implementing any of the other four choices exceeds the value of the harm that would occur if the risk came to fruition. To truly qualify as acceptance, it cannot be a risk where the administrator or manager is unaware of its existence; it has to be an identified risk for which those involved understand the potential cost or damage and agree to accept it. Residual risk is always present and will remain a risk thus it should be accepted (risk acceptance)
QUESTION 123
A software company has completed a security assessment. The assessment states that the company should implement fencing and lighting around the property. Additionally, the assessment states that production releases of their software should be digitally signed. Given the recommendations, the company was deficient in which of the following core security areas? (Select TWO).
A. Fault tolerance
B. Encryption
C. Availability
D. Integrity
E. Safety
F. Confidentiality
Answer: DE
Explanation:
Aspects such as fencing, proper lighting, locks, CCTV, Escape plans Drills, escape routes and testing controls form part of safety controls.
Integrity refers to aspects such as hashing, digital signatures, certificates and non-repudiation – all of which has to do with data integrity.
QUESTION 124
Which of the following defines a business goal for system restoration and acceptable data loss?
A. MTTR
B. MTBF
C. RPO
D. Warm site
Answer: C
Explanation:
The recovery point objective (RPO) defines the point at which the system needs to be restored. This could be where the system was two days before it crashed (whip out the old backup tapes) or five minutes before it crashed (requiring complete redundancy). This is an essential business goal insofar as system restoration and acceptable data loss is concerned.
QUESTION 125
Drag and Drop Question
A Security administrator wants to implement strong security on the company smart phones and terminal servers located in the data center. Drag and Drop the applicable controls to each asset type.
Instructions: Controls can be used multiple times and not all placeholders needs to be filled. When you have completed the simulation, Please select Done to submit.
Answer:
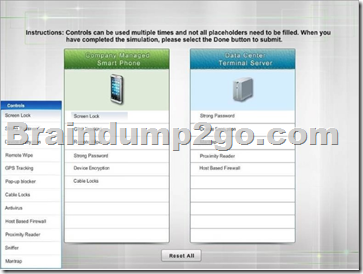
Explanation:
http://www.mentor-app.com/
QUESTION 126
Sara, the Chief Security Officer (CSO), has had four security breaches during the past two years.
Each breach has cost the company $3,000. A third party vendor has offered to repair the security hole in the system for $25,000. The breached system is scheduled to be replaced in five years.
Which of the following should Sara do to address the risk?
A. Accept the risk saving $10,000.
B. Ignore the risk saving $5,000.
C. Mitigate the risk saving $10,000.
D. Transfer the risk saving $5,000.
Answer: D
Explanation:
Risk transference involves sharing some of the risk burden with someone else, such as an insurance company. The cost of the security breach over a period of 5 years would amount to
$30,000 and it is better to save $5,000.
QUESTION 127
Which of the following concepts are included on the three sides of the “security triangle”? (Select THREE).
A. Confidentiality
B. Availability
C. Integrity
D. Authorization
E. Authentication
F. Continuity
Answer: ABC
Explanation:
Confidentiality, integrity, and availability are the three most important concepts in security.
Thus they form the security triangle.
QUESTION 128
Elastic cloud computing environments often reuse the same physical hardware for multiple customers over time as virtual machines are instantiated and deleted. This has important implications for which of the following data security concerns?
A. Hardware integrity
B. Data confidentiality
C. Availability of servers
D. Integrity of data
Answer: B
Explanation:
Data that is not kept separate or segregated will impact on that data’s confidentiality maybe being compromised. Be aware of the fact that your data is only as safe as the data with which it is integrated. For example, assume that your client database is hosted on a server that another company is also using to test an application that they are creating. If their application obtains root- level access at some point (such as to change passwords) and crashes at that point, then the user running the application could be left with root permissions and conceivably be to access data on the server for which they are not authorized, such as your client database.
Data segregation is crucial; keep your data on secure servers.
QUESTION 129
Acme Corp has selectively outsourced proprietary business processes to ABC Services. Due to some technical issues, ABC services wants to send some of Acme Corp’s debug data to a third party vendor for problem resolution. Which of the following MUST be considered prior to sending data to a third party?
A. The data should be encrypted prior to transport
B. This would not constitute unauthorized data sharing
C. This may violate data ownership and non-disclosure agreements
D. Acme Corp should send the data to ABC Services’ vendor instead
Answer: C
Explanation:
With sending your data to a third party is already a risk since the third party may have a different policy than yours. Data ownership and non-disclosure is already a risk that you will have to accept since the data will be sent for debugging /troubleshooting purposes which will result in definite disclosure of the data.
QUESTION 130
An administrator wants to minimize the amount of time needed to perform backups during the week. It is also acceptable to the administrator for restoration to take an extended time frame.
Which of the following strategies would the administrator MOST likely implement?
A. Full backups on the weekend and incremental during the week
B. Full backups on the weekend and full backups every day
C. Incremental backups on the weekend and differential backups every day
D. Differential backups on the weekend and full backups every day
Answer: A
Explanation:
A full backup is a complete, comprehensive backup of all fi les on a disk or server. The full backup is current only at the time it’s performed. Once a full backup is made, you have a complete archive of the system at that point in time. A system shouldn’t be in use while it undergoes a full backup because some fi les may not get backed up. Once the system goes back into operation, the backup is no longer current. A full backup can be a time-consuming process on a large system. An incremental backup is a partial backup that stores only the information that has been changed since the last full or the last incremental backup. If a full backup were performed on a Sunday night, an incremental backup done on Monday night would contain only the information that changed since Sunday night. Such a backup is typically considerably smaller than a full backup. Each incremental backup must be retained until a full backup can be performed. Incremental backups are usually the fastest backups to perform on most systems, and each incremental backup tape is relatively small.
Braindump2go is famous for our Interactive Testing Engine that simulates a real exam environment as experienced on the actual test. We will help you become familiar with the testing environment in advance.Real SY0-401 Exam Questions Plus Real SY0-401 Exam Testing Environment! Braindump2go 100% Guarantees your pass of SY0-401 Exam! SY0-401 Dumps,1220q SY0-401 Exam Questions, SY0-401 PDF and SY0-401 VCE are also available for instant download in our website at any time! 24 hours professional assistance from IT Group! Braindump2go aims to help you pass SY0-401 Exam easily!
FREE DOWNLOAD: NEW UPDATED SY0-401 PDF Dumps & SY0-401 VCE Dumps from Braindump2go: http://www.braindump2go.com/sy0-401.html (1220 Q&A)